Planning guidelines
If you don’t share user and resource information among multiple Mac computers, very little directory domain planning is necessary, because everything can be accessed from a local directory domain.
However, make sure that all individuals who use a Mac computer have user accounts on that computer. These user accounts reside in the local directory domain on the computer.
In addition, everyone who needs to use a OS X Server’s file service, mail service, or other services that require authentication must have a user account in the server’s local directory domain.
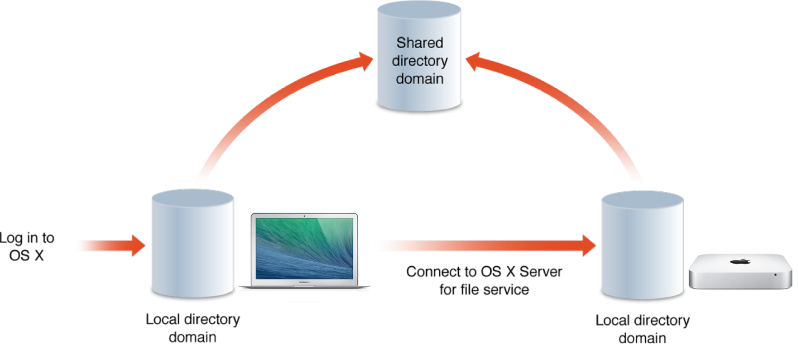
With this arrangement, each user has two accounts, one for logging in to a computer and one for accessing services of a OS X Server, as shown in the following figure.

When a user attempts to access the file service, the file server accesses the shared directory domain to verify the user account. Because the user computer and the file server are connected to the shared directory domain, the user account on the shared directory domain is used to access a computer and the file service without needing a local account on each computer.
The user logs in to the local directory domain of the Mac and then uses a different account to log in to the local directory domain of the file services server.
To share information among Mac computers and servers, you must set up at least one shared directory domain. With this arrangement, each user needs an account only in the shared directory domain.
With this one account, the user can log in to OS X on any computer that’s configured to access the shared directory domain. The user can also use this same account to access services of any OS X Server that’s configured to access the shared directory domain.
The following figure shows a configuration with a shared directory domain. The figure shows a user logging in to a Mac computer using a shared directory domain account. Then the shared directory domain account is also used to access a file service.
In many organizations, a single shared directory domain is adequate. It can handle hundreds of thousands of users and thousands of computers sharing the same resources, such as printer queues, share points for home directories, share points for apps, and share points for documents.
You can replicate the shared directory domain to increase the capacity or performance of the directory system by configuring multiple servers to handle the directory system load for the network.
Larger, more complex organizations can benefit from extra shared directory domains. The following figure shows how one such complex organization might organize its directory domains.
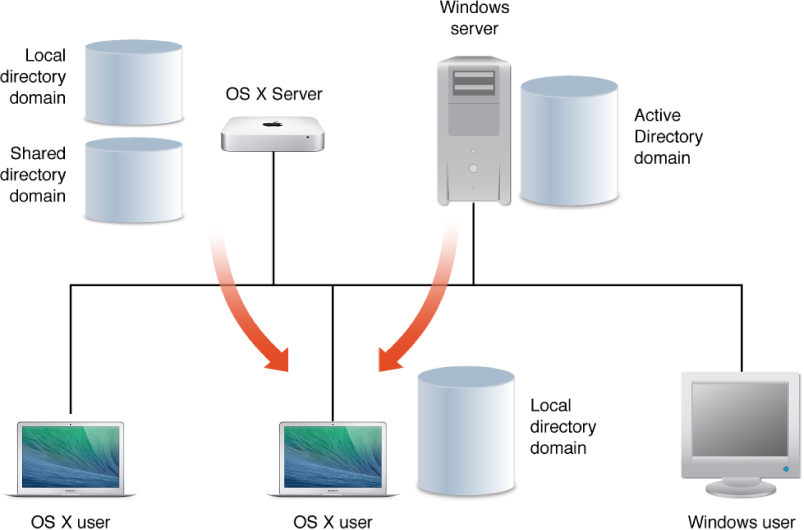
If you have a large organization and you want to increase the performance and capacity of your network directory domain, you can add multiple directory domains to your network. Also, by using multiple directory domains you can load-balance your corporate directory domain.
There are different methods of configuring multiple directory domains. By analyzing your network topology you can determine the best method for your network. The following are optional configurations of multiple directory domains:
Open Directory with an existing domain: You can configure an Open Directory server on a network that has an existing directory domain such as an Active Directory or Open Directory domain.
For example, if your organization has an existing Active Directory server that supports Windows and Mac client computers, you can add an Open Directory server to better support Mac users. The two servers can exist on the same network and provide redundant directory domains for Windows and Mac clients.
You can also configure OS X Server to handle cross-domain authorization if a Kerberos realm exists.
If you have an existing Active Directory server, you can connect an Open Directory server to it and easily add users from the Active Directory server to your Open Directory server. These users are referred to as augment users.
Open Directory master server with replicas: You can create an Open Directory master server with replicas. The replica servers have a copy of the Open Directory master’s directory domain for load balancing and redundancy.
For example, your organization could have an Open Directory master at your headquarters and place replicas of that server at each remote location. This prevents users at remote locations from experiencing delayed logins.
Cascading replication: You can use cascading replication, where replicas of an Open Directory master have replicas. If a replica is a direct member of the Open Directory master and it has replicas it’s called a relay.
For example, if your organization has 32 replicas and you must add another replica, you can reorganize your network topology and have your replicas become relays by adding replicas to a replica (or relay).
Cascading replication load balances the Open Directory master by minimizing the number of replicas it must directly manage.
