Kerberos authentication process
There are several phases to Kerberos authentication. In the first phase, the client obtains credentials to be used to request access to Kerberized services. In the second phase, the client requests authentication for a specific service. In the final phase, the client presents those credentials to the service.
The following illustration summarizes these activities. The service and the client can be the same entity (such as the login window) or two entities (such as a mail client and the mail server).
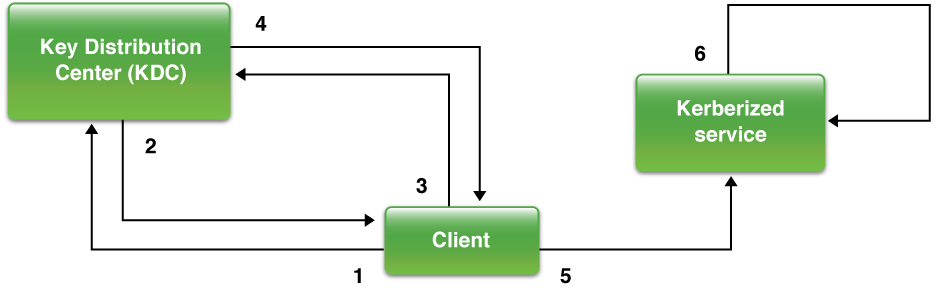
The client authenticates to a Kerberos KDC, which interacts with realms to access authentication data.
This is the only step in which passwords and associated password policy information are checked.
The KDC issues a ticket-granting ticket to the client.
The ticket is the credential needed when the client wants to use Kerberized services and is good for a configurable period of time, but it can be revoked before expiration. It’s cached on the client until it expires.
The client contacts the KDC with the ticket-granting ticket when it wants to use a Kerberized service.
The KDC issues a ticket for that service.
The client presents the ticket to the service.
The service authenticates the client by verifying that the ticket is valid.
After authenticating the client, the service determines if the client is authorized to use the service.
Kerberos authenticates clients, but it doesn’t authorize them to use services. For example, many services use a Mac server’s service access control lists (SACLs) to determine whether a client is authorized to use the service.
Kerberos never sends a password or password policy information to a service. After a ticket-granting ticket is obtained, no password information is provided.
Time is very important with Kerberos. If the client and the KDC are out of sync by more than a few minutes, the client fails to achieve authentication with the KDC. The date, time, and time zone information must be correct on the KDC server and clients, and the server and clients should all use the same network time service to keep their clocks in sync.
For more information about Kerberos, see the MIT Kerberos website at web.mit.edu/kerberos/www/index.html.
